SSLScan comprueba la seguridad de tu SSL, siempre se ha dicho que es más fácil ser atacante que no defensor. El que ataca normalmente buscará todos los vectores de entrada posible, cuando crea que ha encontrado uno lo atacará.
El defensor en cambio solo le resta ir revisando sus niveles de seguridad para que no le ataquen.
Tabla de Contenido
Una de las cosas que se han de revisar es el SSL, desde hace dos años están saliendo ataques relacionados con él y no está de más revisar el SSL de nuestros servidores en la DMZ y en los servidores internos.
SSLScan comprueba la seguridad de tu SSL instalar
Una de las herramientas que nos pueden ayudar es sslscan.
En distribuciones como Ubuntu lo podremos instalar haciendo
apt-get install sslscan
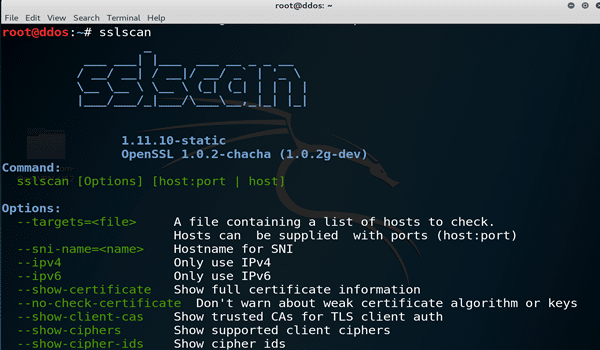
Una vez instalado, lo iniciamos y vemos las opciones disponibles.
darkmac:~ marc$ sslscan _ ___ ___| |___ ___ __ _ _ __ / __/ __| / __|/ __/ _` | '_ \ \__ \__ \ \__ \ (_| (_| | | | | |___/___/_|___/\___\__,_|_| |_| Version 1.8.0 http://www.titania.co.uk Copyright Ian Ventura-Whiting 2009 SSLScan is a fast SSL port scanner. SSLScan connects to SSL ports and determines what ciphers are supported, which are the servers prefered ciphers, which SSL protocols are supported and returns the SSL certificate. Client certificates / private key can be configured and output is to text / XML. Command: sslscan [Options] [host:port | host] Options: --targets=<file> A file containing a list of hosts to check. Hosts can be supplied with ports (i.e. host:port). --no-failed List only accepted ciphers (default is to listing all ciphers). --ssl2 Only check SSLv2 ciphers. --ssl3 Only check SSLv3 ciphers. --tls1 Only check TLSv1 ciphers. --pk=<file> A file containing the private key or a PKCS#12 file containing a private key/certificate pair (as produced by MSIE and Netscape). --pkpass=<password> The password for the private key or PKCS#12 file. --certs=<file> A file containing PEM/ASN1 formatted client certificates. --starttls If a STARTTLS is required to kick an SMTP service into action. --http Test a HTTP connection. --bugs Enable SSL implementation bug work- arounds. --xml=<file> Output results to an XML file. --version Display the program version. --help Display the help text you are now reading. Example: sslscan 127.0.0.1</blockquote> Como veis nos permite afinar el tipo de escaneo, además podemos incluso exportar los resultados. Vamos a escanear una página cualquiera:<blockquote>darkmac:~ marc$ sslscan www.minhacienda.gov.co _ ___ ___| |___ ___ __ _ _ __ / __/ __| / __|/ __/ _` | '_ \ \__ \__ \ \__ \ (_| (_| | | | | |___/___/_|___/\___\__,_|_| |_| Version 1.8.0 http://www.titania.co.uk Copyright Ian Ventura-Whiting 2009 Testing SSL server www.minhacienda.gov.co on port 443 Supported Server Cipher(s): Rejected N/A SSLv2 168 bits DES-CBC3-MD5 Rejected N/A SSLv2 56 bits DES-CBC-MD5 Rejected N/A SSLv2 40 bits EXP-RC2-CBC-MD5 Rejected N/A SSLv2 128 bits RC2-CBC-MD5 Accepted SSLv2 40 bits EXP-RC4-MD5 Accepted SSLv2 128 bits RC4-MD5 Rejected N/A SSLv3 128 bits ADH-SEED-SHA Rejected N/A SSLv3 128 bits DHE-RSA-SEED-SHA Rejected N/A SSLv3 128 bits DHE-DSS-SEED-SHA Rejected N/A SSLv3 128 bits SEED-SHA Rejected N/A SSLv3 256 bits ADH-AES256-SHA Rejected N/A SSLv3 256 bits DHE-RSA-AES256-SHA Rejected N/A SSLv3 256 bits DHE-DSS-AES256-SHA Rejected N/A SSLv3 256 bits AES256-SHA Rejected N/A SSLv3 128 bits ADH-AES128-SHA Rejected N/A SSLv3 128 bits DHE-RSA-AES128-SHA Rejected N/A SSLv3 128 bits DHE-DSS-AES128-SHA Rejected N/A SSLv3 128 bits AES128-SHA Accepted SSLv3 168 bits ADH-DES-CBC3-SHA Accepted SSLv3 56 bits ADH-DES-CBC-SHA Rejected N/A SSLv3 40 bits EXP-ADH-DES-CBC-SHA Accepted SSLv3 128 bits ADH-RC4-MD5 Rejected N/A SSLv3 40 bits EXP-ADH-RC4-MD5 Rejected N/A SSLv3 168 bits EDH-RSA-DES-CBC3-SHA Rejected N/A SSLv3 56 bits EDH-RSA-DES-CBC-SHA Rejected N/A SSLv3 40 bits EXP-EDH-RSA-DES-CBC-SHA Rejected N/A SSLv3 168 bits EDH-DSS-DES-CBC3-SHA Rejected N/A SSLv3 56 bits EDH-DSS-DES-CBC-SHA Rejected N/A SSLv3 40 bits EXP-EDH-DSS-DES-CBC-SHA Accepted SSLv3 168 bits DES-CBC3-SHA Accepted SSLv3 56 bits DES-CBC-SHA Accepted SSLv3 40 bits EXP-DES-CBC-SHA Rejected N/A SSLv3 40 bits EXP-RC2-CBC-MD5 Accepted SSLv3 128 bits RC4-SHA Accepted SSLv3 128 bits RC4-MD5 Accepted SSLv3 40 bits EXP-RC4-MD5 Rejected N/A SSLv3 0 bits NULL-SHA Rejected N/A SSLv3 0 bits NULL-MD5 Failed N/A TLSv1 128 bits ADH-SEED-SHA Failed N/A TLSv1 128 bits DHE-RSA-SEED-SHA Failed N/A TLSv1 128 bits DHE-DSS-SEED-SHA Failed N/A TLSv1 128 bits SEED-SHA Failed N/A TLSv1 256 bits ADH-AES256-SHA Failed N/A TLSv1 256 bits DHE-RSA-AES256-SHA Failed N/A TLSv1 256 bits DHE-DSS-AES256-SHA Failed N/A TLSv1 256 bits AES256-SHA Failed N/A TLSv1 128 bits ADH-AES128-SHA Failed N/A TLSv1 128 bits DHE-RSA-AES128-SHA Failed N/A TLSv1 128 bits DHE-DSS-AES128-SHA Failed N/A TLSv1 128 bits AES128-SHA Failed N/A TLSv1 168 bits ADH-DES-CBC3-SHA Failed N/A TLSv1 56 bits ADH-DES-CBC-SHA Failed N/A TLSv1 40 bits EXP-ADH-DES-CBC-SHA Failed N/A TLSv1 128 bits ADH-RC4-MD5 Failed N/A TLSv1 40 bits EXP-ADH-RC4-MD5 Failed N/A TLSv1 168 bits EDH-RSA-DES-CBC3-SHA Failed N/A TLSv1 56 bits EDH-RSA-DES-CBC-SHA Failed N/A TLSv1 40 bits EXP-EDH-RSA-DES-CBC-SHA Failed N/A TLSv1 168 bits EDH-DSS-DES-CBC3-SHA Failed N/A TLSv1 56 bits EDH-DSS-DES-CBC-SHA Failed N/A TLSv1 40 bits EXP-EDH-DSS-DES-CBC-SHA Failed N/A TLSv1 168 bits DES-CBC3-SHA Failed N/A TLSv1 56 bits DES-CBC-SHA Failed N/A TLSv1 40 bits EXP-DES-CBC-SHA Failed N/A TLSv1 40 bits EXP-RC2-CBC-MD5 Failed N/A TLSv1 128 bits RC4-SHA Failed N/A TLSv1 128 bits RC4-MD5 Failed N/A TLSv1 40 bits EXP-RC4-MD5 Failed N/A TLSv1 0 bits NULL-SHA Failed N/A TLSv1 0 bits NULL-MD5 Prefered Server Cipher(s): SSLv2 40 bits EXP-RC4-MD5 SSLv3 168 bits ADH-DES-CBC3-SHA SSL Certificate:
Lanzando escaneo
El output generado es un poco feo, en el sentido de que nos ha sacado las pruebas fallidas, vamos a lanzar el escaneo y que solo nos extraiga los datos útiles.
darkmac:~ marc$ sslscan --no-failed www.agenciatributaria.gob.es _ ___ ___| |___ ___ __ _ _ __ / __/ __| / __|/ __/ _` | '_ \ \__ \__ \ \__ \ (_| (_| | | | | |___/___/_|___/\___\__,_|_| |_| Version 1.8.0 http://www.titania.co.uk Copyright Ian Ventura-Whiting 2009 Testing SSL server www.agenciatributaria.gob.es on port 443 Supported Server Cipher(s): Accepted SSLv3 256 bits AES256-SHA Accepted SSLv3 128 bits AES128-SHA Accepted SSLv3 168 bits DES-CBC3-SHA Accepted SSLv3 128 bits RC4-SHA Accepted SSLv3 128 bits RC4-MD5 Accepted TLSv1 256 bits AES256-SHA Accepted TLSv1 128 bits AES128-SHA Accepted TLSv1 168 bits DES-CBC3-SHA Accepted TLSv1 128 bits RC4-SHA Accepted TLSv1 128 bits RC4-MD5 Prefered Server Cipher(s): SSLv3 128 bits RC4-SHA TLSv1 128 bits RC4-SHA SSL Certificate: Version: 2 Serial Number: 2954 Signature Algorithm: sha1WithRSAEncryption Issuer: /C=ES/O=FNMT-RCM/OU=AC APE Not valid before: Jan 11 11:50:38 2010 GMT Not valid after: Jan 11 11:50:38 2014 GMT Subject: /C=es/O=FNMT-RCM/OU=AC APE/OU=500070015/CN=www.agenciatributaria.gob.es Public Key Algorithm: rsaEncryption RSA Public Key: (2048 bit) Modulus (2048 bit): 00:b1:5d:5f:64:28:89:24:58:03:37:d7:da:99:35: b6:7a:69:e0:9d:c8:99:d3:65:14:60:41:78:0b:04: 66:bd:ef:9e:86:b2:5e:6f:b0:ad:61:3b:a3:7e:a2: 55:3b:40:e9:2e:39:3c:95:dc:f8:5e:3f:c9:d3:f0: 28:32:9a:0f:ec:c7:da:b6:30:85:fd:0b:09:81:53: a7:93:c6:fa:b6:ba:3f:82:9f:c6:b9:43:dc:1e:88: 8d:7a:1f:31:9b:a9:de:ea:60:60:10:8a:fa:a8:2b: 8b:bc:a6:0a:ff:64:92:c8:a5:df:43:35:33:4a:13: fa:a4:d3:f6:92:86:e3:16:fd:2f:a7:8b:52:7a:24: f5:43:1e:01:c7:bc:60:be:24:95:05:d7:1e:15:99: 4d:83:2c:74:26:aa:81:98:ad:60:48:8b:bc:71:cc: 19:8a:cb:9f:43:ac:d0:8e:2c:41:be:17:8b:6e:6b: a5:b4:f8:e3:55:a8:c1:45:5f:15:0d:38:85:f6:5d: da:f3:ff:41:90:99:38:84:c5:53:30:ab:a5:a9:12: 12:e0:cf:43:fa:57:8f:17:51:2a:5d:c5:55:59:7b: e5:21:78:96:68:36:4d:7e:4a:9f:be:06:01:6d:77: 84:73:ec:d3:13:82:fe:09:00:60:64:e8:0e:4e:97: 47:17 Exponent: 65537 (0x10001) X509v3 Extensions: X509v3 Subject Alternative Name: DirName:/1.3.6.1.4.1.5734.1.15=Q2826000H/1.3.6.1.4.1.5734.1.14=AGENCIA ESTATAL DE ADMINISTRACI\xD3N TRIBUTARIA/1.3.6.1.4.1.5734.1.8=www.agenciatributaria.gob.es, DNS:www.agenciatributaria.gob.es X509v3 Basic Constraints: critical CA:FALSE X509v3 Key Usage: critical Digital Signature, Key Encipherment X509v3 Subject Key Identifier: 49:22:23:54:F3:4C:96:92:42:00:43:E5:51:72:BD:39:B6:4A:0F:8A X509v3 Authority Key Identifier: keyid:63:4B:74:5B:07:BF:E8:66:D1:5A:2C:5F:CB:F9:79:6E:A0:8C:AE:27 Netscape Cert Type: SSL Server, S/MIME X509v3 Certificate Policies: Policy: 1.3.6.1.4.1.5734.3.12 CPS: http://www.cert.fnmt.es/dpcs/ User Notice: Explicit Text: Sujeto a las condiciones de uso expuestas en la Declaraci?n de Pr?cticas de Certificaci?n de la FNMT-RCM (C/Jorge Juan 106-28009-Madrid-Espa?a) 1.3.6.1.4.1.5734.1.33: ..SEDE ELECTRONICA qcStatements: 0.0......F..0......F..0...EUR......0......F..... Authority Information Access: OCSP - URI:http://ocspape.cert.fnmt.es/ocspape/OcspResponder CA Issuers - URI:http://www.cert.fnmt.es/certs/ACRAIZFNMT.crt X509v3 Extended Key Usage: TLS Web Server Authentication X509v3 CRL Distribution Points: URI:ldap://ldapape.cert.fnmt.es/CN=CRL9,OU=AC%20APE,O=FNMT-RCM,C=ES?certificateRevocationList;binary?base?objectclass=cRLDistributionPoint URI:http://www.cert.fnmt.es/crlsape/CRL9.crl Verify Certificate: unable to get local issuer certificate
Como veis, ha sacado los datos útiles por pantalla.
Consulta del ataque Crime
Una de las cosas más interesantes de la herramienta es que permite cargarle un fichero con una lista de dominios para poder escamar uno detrás del otro.
Unos de los ataques mas sonados en SSL es el ataque Crime, la presentación sobre el ataque la podéis consultar aquí => http://netifera.com/research/crime/CRIME_ekoparty2012.pdf
En el artículo de hoy SSLScan comprueba la seguridad de tu SSL, hemos aprendido a usar SSLScan para comprobar la seguridad SSL de tus servidores.
También puede ser de tu interes – https://www.dragonjar.org/extraer-objetos-flash-de-documentos-office-maliciosos.xhtml


