Fake Skype analysis
 Fake Skype analysis, es común por parte de los criminales imitar programas legítimos para tratar de infectar usuarios. Si consiguen crear una buena imitación de un software muy usado se podrá conseguir un impacto muy alto.
Fake Skype analysis, es común por parte de los criminales imitar programas legítimos para tratar de infectar usuarios. Si consiguen crear una buena imitación de un software muy usado se podrá conseguir un impacto muy alto.
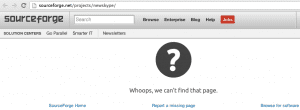
En una lista de seguridad advertían de que habían subido a un repositorio de Sourceforge un instalador de Skype malicioso. Antes de que de retiraran el archivo me lo descargue para ver que es lo que era exactamente.
Fake Skype analysis y el archivo de Sourceforge
Por suerte el archivo ya ha sido removido del repositorio de Sourceforge.
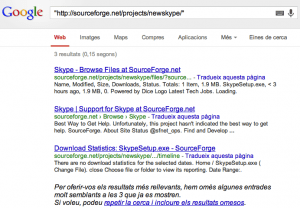
Si buscamos en Google, podemos ver que ya había sido cacheado por él.
El MD5 del binario es:
darkmac:pyew marc$ md5 ../../../Downloads/SkypeSetup.exe
MD5 (../../../Downloads/SkypeSetup.exe) = 4e6e4f03ae39c1273a7dd64c57ff2099
Antes de ejecutarlo en ningún entorno vamos a extraer algunos strings del binario.
Entre los strings encontramos cosas como:
OleInitialize ole32.dll OLEAUT32.dll WINRAR.SFX RSDSo d:\Projects\WinRAR\SFX\build\sfxrar32\Release\sfxrar.pdb
Presuntamente podemos ver que se estaba compilando el archivo en la Unidad D:
Podemos ver mas strings interesantes
</assembly> PADDINGXXPADDINGPADDINGXXPADDINGPADDINGXXPADDINGPADDINGXXPADDINGPADDINGXXPADDINGPADDINGXXPADDINGPADDINGXXPADDINGPADDINGXXPADDINGPADDINGXXPADDINGPADDINGXXPADDINGPADDINGXXPADDINGPADDINGXXPADDINGPADDINGXXPADDING***messages*** ; Strings 28b64ee0="Selecione a pasta de destino" c2f7663d="Extraindo %s" e6184908="Ignorando %s" 5ec2b9a4="Final inesperado do arquivo" 8e950692="O cabe alho do arquivo \"%s\" est corrompido" 7e3a9609="O cabe alho do coment rio do arquivo est corrompido" 4eb4cd58="O coment rio do arquivo est corrompido" 009537bf="Mem ria insuficiente" 4d117d42="M todo desconhecido em %s" 7c1e30d8="N o foi poss vel abrir %s" 62240658="N o foi poss vel criar %s" 644f7b2f="N o foi poss vel criar a pasta %s" efa47afe="Falha de CRC no arquivo codificado %s. Arquivo corrompido ou senha errada." 2669d7b6="Falha de CRC em %s" cedc96f3="Falha de CRC nos dados comprimidos em %s" d7b7d4f4="Senha incorreta para %s" 41ce4b30="Erro de grava o no arquivo %s. Provavelmente o disco est cheio" 68a8444a="Erro de leitura no arquivo %s" fc92e4b0="Erro ao fechar o arquivo" c282ae83="O volume requerido est ausente" 8deeac82="Este arquivo est em formato desconhecido ou danificado" bdba36ee="Extraindo de %s" 3f75c3f0="Pr ximo volume" b127402c="O cabe alho do arquivo est corrompido" 28968711="Fechar" 664abaa4="Erro" f819b84b="Foram encontrados erros ao executar a opera o\nAten o para a informa o da janela para maiores detalhes" 4bcf6a1f="bytes" 0fafb862="modificado em" a05a6a8d="pasta n o est acess vel" ca228992="Alguns arquivos n o puderam ser criados.\nFavor fechar todas as aplica es, reinicie o Windows e recomece a instala 7b70360d="Alguns arquivos da instala o est o corrompidos.\nFavor fazer o download de um novo arquivo para refazer a instala 3bf460be="Todos os arquivos" 4ebc6a80="<ul><li>Pressione o bot o <b>Instalar</b> para iniciar a extra o.</li><br><br>" 501aec0e="<ul><li>Pressione o bot o <b>Extrair</b> para iniciar a extra o.</li><br><br>" bf41b9e0="<li>Use o bot o <b>Procurar</b> para selecionar uma pasta de"
Estos strings pertenecerían al asistente de instalación de Skype.
Ahora usaremos una tool. que se llama pyew, para extraer mas información del binario.
Ejecutamos la herramienta.
darkmac:pyew marc$ python pyew.py ../../../Downloads/SkypeSetup.exe
Cuando ejecutemos la herramienta sobre el binario nos arrojará información sobre el archivo PE.
PE Information
Sections:
.text 0x1000 0x116de 71680
.rdata 0x13000 0x1c05 7680
.data 0x15000 0xff2c 512
.CRT 0x25000 0x10 512
.rsrc 0x26000 0x13530 79360
Entry Point at 0xa6ec
Virtual Address is 0x40b2ec
Code Analysis ...
Analyzing address 0x0000a5d4 - 0 in queue / 3 total
0000 4D 5A 90 00 03 00 00 00 04 00 00 00 FF FF 00 00 MZ..............
0010 B8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 ........@.......
0020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0030 00 00 00 00 00 00 00 00 00 00 00 00 E8 00 00 00 ................
0040 0E 1F BA 0E 00 B4 09 CD 21 B8 01 4C CD 21 54 68 ........!..L.!Th
0050 69 73 20 70 72 6F 67 72 61 6D 20 63 61 6E 6E 6F is program canno
0060 74 20 62 65 20 72 75 6E 20 69 6E 20 44 4F 53 20 t be run in DOS
0070 6D 6F 64 65 2E 0D 0D 0A 24 00 00 00 00 00 00 00 mode....$.......
0080 D3 ED 15 06 97 8C 7B 55 97 8C 7B 55 97 8C 7B 55 ......{U..{U..{U
0090 9E F4 E8 55 82 8C 7B 55 97 8C 7A 55 3A 8C 7B 55 ...U..{U..zU:.{U
00A0 89 DE EE 55 92 8C 7B 55 9E F4 F8 55 9E 8C 7B 55 ...U..{U...U..{U
00B0 9E F4 FF 55 BA 8C 7B 55 9E F4 E9 55 96 8C 7B 55 ...U..{U...U..{U
00C0 9E F4 EF 55 96 8C 7B 55 9E F4 EA 55 96 8C 7B 55 ...U..{U...U..{U
00D0 52 69 63 68 97 8C 7B 55 00 00 00 00 00 00 00 00 Rich..{U........
00E0 00 00 00 00 00 00 00 00 50 45 00 00 4C 01 05 00 ........PE..L...
00F0 52 8C 0B 4D 00 00 00 00 00 00 00 00 E0 00 03 01 R..M............
0100 0B 01 09 00 00 18 01 00 00 58 01 00 00 00 00 00 .........X......
0110 EC B2 00 00 00 10 00 00 00 30 01 00 00 00 40 00 .........0....@.
0120 00 10 00 00 00 02 00 00 05 00 00 00 00 00 00 00 ................
0130 05 00 00 00 00 00 00 00 00 A0 03 00 00 04 00 00 ................
0140 00 00 00 00 02 00 00 85 00 00 10 00 00 10 00 00 ................
0150 00 00 10 00 00 10 00 00 00 00 00 00 10 00 00 00 ................
0160 80 4B 01 00 33 00 00 00 30 3C 01 00 DC 00 00 00 .K..3...0<......
0170 00 60 02 00 30 35 01 00 00 00 00 00 00 00 00 00 .`..05..........
0180 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0190 C0 32 01 00 1C 00 00 00 00 00 00 00 00 00 00 00 .2..............
01A0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
01B0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
01C0 00 30 01 00 C0 02 00 00 00 00 00 00 00 00 00 00 .0..............
01D0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
01E0 2E 74 65 78 74 00 00 00 DE 16 01 00 00 10 00 00 .text...........
01F0 00 18 01 00 00 04 00 00 00 00 00 00 00 00 00 00 ................
[0x00000000:0x00400000]>
La cabecera MZ, indica que se trata de un ejecutable.
Tenemos un promtp desde el que podremos ejecutar ciertos comandos para sacar mas información útil.
Aunque los strings anteriores los hemos extraído del comando strings, con pyew podremos buscar strings en concreto en el binario.
[0x00000000:0x00400000]> /s skype
HINT[0x00028473]: skype.exe..{.-.....U..U...i.........s.......n rf..W.(.!zJ)3.
HINT[0x00195cda]: skype.cpl....j.....YU..Q...>.....~g..V.......Pp(....i.!.!...
[0x00000000:0x00400000]> /s microsoft
HINT[0x00026dce]: microsoft-com:asm.v1" manifestVersion="1.0">..<assemblyIdent
HINT[0x00026eb4]: microsoft-com:asm.v2">.. <security>.. <requestedPrivileg
HINT[0x000270c8]: microsoft-com:compatibility.v1">.. <application>.. <!--T
HINT[0x0002725f]: microsoft-com:asm.v3">.. <asmv3:windowsSettings xmlns="http
HINT[0x000272a6]: microsoft.com/SMI/2005/WindowsSettings">.. <dpiAware>true
[0x00000000:0x00400000]>
Desde pyew, podremos buscar si el archivo está en Virus Total.
[0x00000000:0x00400000]> vt File ../../../Downloads/SkypeSetup.exe with MD5 4e6e4f03ae39c1273a7dd64c57ff2099 -------------------------------------------------------------------------------- McAfee : Artemis!4E6E4F03AE39 Malwarebytes : Trojan.Agent.CPL K7AntiVirus : Spyware K7GW : Spyware Norman : Suspicious.FXZ ESET-NOD32 : probably a variant of Win32/TrojanDownloader.Banload.SEL TrendMicro-HouseCall : TROJ_GEN.R04AH01GC13 Avast : Win32:Malware-gen Kaspersky : HEUR:Trojan.Win32.Generic BitDefender : Gen:Variant.Symmi.17535 Emsisoft : Gen:Variant.Symmi.17535 (B) Comodo : UnclassifiedMalware F-Secure : Gen:Variant.Symmi.17535 DrWeb : BackDoor.Infector.50 VIPRE : Trojan.Win32.Generic!BT AntiVir : TR/Spy.Banker.acn.709 McAfee-GW-Edition : Artemis!4E6E4F03AE39 Sophos : Troj/Delp-P Antiy-AVL : Trojan/Win32.Rozena Kingsoft : Win32.Troj.Undef.(kcloud) Microsoft : TrojanSpy:Win32/Banker.ACN GData : Gen:Variant.Symmi.17535 Ikarus : Trojan-Spy.Win32.Banker AVG : PSW.Banker6.AYEI Panda : Trj/CI.A [0x00000000:0x00400000]>
Alguien ya subió el archivo a Virus Total.
Análisis dinámico de la muestra SIN INTERNET
Aunque habitualmente subo el malware a mi sandbox con Cuckoo, esta vez he decidido usar una sandbox que me he montado. La sandbox es bien conocida por vosotros lectores, se trata de BSA (Buster sandbox analyzer).
Con esta sandbox puedo obtener rápidamente información interesante de lo que hace la muestra.
Para quien no lo sepa el ejecutar el malware en la sandbox de BSA, lo que hace realmente es ejecutar el sample en sandboxie.
BSA recoge los cambios que se han hecho y te los muestra en un report.
[ General information ]
* Analysis duration: 00:00:13
* File name: c:\documents and settings\user\desktop\malware\skypesetup.exe
[ Changes to filesystem ]
* Creates file (hidden) C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Feeds Cache\desktop.ini
* Creates file C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Internet Explorer\Recovery\Active\{ADDE1BD4-EC93-11E2-8F9B-0800274FAA0E}.dat
* Creates file C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Internet Explorer\Recovery\Last Active\RecoveryStore.{ADDE1BD6-EC93-11E2-8F9B-0800274FAA0E}.dat
* Creates file C:\Documents and Settings\user\Local Settings\Application Data\Microsoft\Internet Explorer\Recovery\Last Active\{ADDE1BD7-EC93-11E2-8F9B-0800274FAA0E}.dat
* Modifies file (hidden) C:\Documents and Settings\user\Local Settings\History\History.IE5\index.dat
* Creates hidden folder C:\Documents and Settings\user\Local Settings\History\History.IE5\MSHist012013071420130715
* Creates file (hidden) C:\Documents and Settings\user\Local Settings\History\History.IE5\MSHist012013071420130715\index.dat
* Creates file C:\Documents and Settings\user\Local Settings\Temp\install.bat
* Creates file C:\Documents and Settings\user\Local Settings\Temp\install_skype.exe
* Creates file C:\Documents and Settings\user\Local Settings\Temp\setup.cpl
* Creates file C:\Documents and Settings\user\Local Settings\Temp\setup_skype.cpl
* Creates file C:\Documents and Settings\user\Local Settings\Temp\Skype.msi
* Creates file C:\Documents and Settings\user\Local Settings\Temporary Internet Files\AntiPhishing\2CEDBFBC-DBA8-43AA-B1FD-CC8E6316E3E2.dat
* Creates file C:\Documents and Settings\user\Local Settings\Temporary Internet Files\Content.IE5\5INHMPF5\st[1].htm
* Modifies file (hidden) C:\Documents and Settings\user\Local Settings\Temporary Internet Files\Content.IE5\index.dat
* Creates file C:\Documents and Settings\user\Local Settings\Temporary Internet Files\Content.IE5\TUBOCA54\downloading[1].htm
* Creates file C:\Documents and Settings\user\Local Settings\Temporary Internet Files\Content.IE5\Z4LDT046\favicon[1].htm
En este primer bloque, podemos ver los cambios que se han producido a nivel de sistema de archivos.
BSA también nos muestra los cambios del registro.
[ Changes to registry ]
* Modifies value "NukeOnDelete=00000001" in key HKEY_LOCAL_MACHINE\software\microsoft\Windows\CurrentVersion\Explorer\BitBucket
old value empty
* Creates value "BINGSRCHFF=00000007" in key HKEY_LOCAL_MACHINE\software\Skype\Installer
* Creates value "BINGSRCHIE=000000FF" in key HKEY_LOCAL_MACHINE\software\Skype\Installer
* Creates value "BINGSRCHGC=00000007" in key HKEY_LOCAL_MACHINE\software\Skype\Installer
* Creates value "MSNHPFF=00000007" in key HKEY_LOCAL_MACHINE\software\Skype\Installer
* Creates value "MSNHPIE=000000FF" in key HKEY_LOCAL_MACHINE\software\Skype\Installer
* Creates value "MSNHPGC=00000007" in key HKEY_LOCAL_MACHINE\software\Skype\Installer
* Creates value "YHP=00000007" in key HKEY_LOCAL_MACHINE\software\Skype\Installer
* Creates value "YSRCH=00000007" in key HKEY_LOCAL_MACHINE\software\Skype\Installer
* Creates value "C2CFF=00000008" in key HKEY_LOCAL_MACHINE\software\Skype\Installer
* Creates value "C2CIE=000000FF" in key HKEY_LOCAL_MACHINE\software\Skype\Installer
* Creates value "C2CGC=00000008" in key HKEY_LOCAL_MACHINE\software\Skype\Installer
* Creates value "DonwloadLastModified=12150" in key HKEY_LOCAL_MACHINE\software\Skype\Installer
binary data=310032003100350030000000
* Creates value "DownloadContentLength=0000E961" in key HKEY_LOCAL_MACHINE\software\Skype\Installer
* Creates value "DownloadETag=12150" in key HKEY_LOCAL_MACHINE\software\Skype\Installer
binary data=310032003100350030000000
* Creates value "InstallExitCode=0000C354" in key HKEY_LOCAL_MACHINE\software\Skype\Phone\UI
* Creates value "SkypeSetup=SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce" in key HKEY_LOCAL_MACHINE\software\Skype\Phone\UI\General
binary data=53004F004600540057004100520045005C004D006900630072006F0073006F00660074005C00570069006E0064006F00770073005C00430075007200720065006E007400560065007200730069006F006E005C00520075006E004F006E00630065000000
* Modifies value "Window_Placement=2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF020000000200000080020000C2010000" in key HKEY_CURRENT_USER\software\Microsoft\Internet Explorer\Main
old value "Window_Placement=2C0000000200000003000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF020000000200000080020000C2010000"
* Modifies value "Version=WS scopes not configured" in key HKEY_CURRENT_USER\software\Microsoft\Internet Explorer\Main\WindowsSearch
binary data=570053002000730063006F0070006500730020006E006F007400200063006F006E0066006900670075007200650064000000
old value "Version=04.00.6001.503"
binary data=300034002E00300030002E0036003000300031002E003500300033000000
* Creates value "Order=08000000020000000C0000000100000000000000" in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Explorer\MenuOrder\Favorites\Links
* Creates value "Type=00000003" in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore
* Creates value "Count=00000001" in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore
* Creates value "Time=DD07070000000E000E002B0001008C00" in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore
* Creates value "LoadTime=00000001" in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore
* Creates value "Type=00000004" in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Ext\Stats\{CF819DA3-9882-4944-ADF5-6EF17ECF3C6E}\iexplore
* Creates value "Count=00000001" in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Ext\Stats\{CF819DA3-9882-4944-ADF5-6EF17ECF3C6E}\iexplore
* Creates value "Time=DD07070000000E000E002B0000007A03" in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Ext\Stats\{CF819DA3-9882-4944-ADF5-6EF17ECF3C6E}\iexplore
* Creates value "Type=00000003" in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Ext\Stats\{DBC80044-A445-435B-BC74-9C25C1C588A9}\iexplore
* Creates value "Count=00000001" in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Ext\Stats\{DBC80044-A445-435B-BC74-9C25C1C588A9}\iexplore
* Creates value "Time=DD07070000000E000E002B0001008C00" in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Ext\Stats\{DBC80044-A445-435B-BC74-9C25C1C588A9}\iexplore
* Creates value "Type=00000004" in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Ext\Stats\{E2E2DD38-D088-4134-82B7-F2BA38496583}\iexplore
* Creates value "Count=00000001" in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Ext\Stats\{E2E2DD38-D088-4134-82B7-F2BA38496583}\iexplore
* Creates value "Time=DD07070000000E000E002B0000007A03" in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Ext\Stats\{E2E2DD38-D088-4134-82B7-F2BA38496583}\iexplore
* Creates value "CachePath=%USERPROFILE%\Local Settings\History\History.IE5\MSHist012013071420130715" in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Extensible Cache\MSHist012013071420130715
binary data=25005500530045005200500052004F00460049004C00450025005C004C006F00630061006C002000530065007400740069006E00670073005C0048006900730074006F00720079005C0048006900730074006F00720079002E004900450035005C004D00530048006900730074003000310032003000310033003000370031003400320030003100330030003700310035000000
* Creates value "CachePrefix=:2013071420130715: " in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Extensible Cache\MSHist012013071420130715
binary data=3A0032003000310033003000370031003400320030003100330030003700310035003A0020000000
* Creates value "CacheLimit=00002000" in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Extensible Cache\MSHist012013071420130715
* Creates value "CacheOptions=0000000B" in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Extensible Cache\MSHist012013071420130715
* Modifies value "SavedLegacySettings=46000000C6000000010000000E0000003132372E302E302E313A3830383000000000000000000000000000000000804A0D0AE81FCE010000000000000000000000000100000002000000AC1201A8000000000000000001000000050000000871190070571A000000000010010000FFFFFFFF000000000C00000000000000010000000000000000000000000000000000000003A8020000000000C000000000000046409D05229E7ECF11AE5A00AA00A7112B770069006E0064006F0077007300000000000000" in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections
old value "SavedLegacySettings=46000000C0000000010000000E0000003132372E302E302E313A3830383000000000000000000000000000000000804A0D0AE81FCE010000000000000000000000000100000002000000AC1201A8000000000000000001000000050000000871190070571A000000000010010000FFFFFFFF000000000C00000000000000010000000000000000000000000000000000000003A8020000000000C000000000000046409D05229E7ECF11AE5A00AA00A7112B770069006E0064006F0077007300000000000000"
* Creates value "Skype="C:\Program Files\Skype\Phone\Skype.exe" /minimized /regrun" in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Run
binary data=220043003A005C00500072006F006700720061006D002000460069006C00650073005C0053006B007900700065005C00500068006F006E0065005C0053006B007900700065002E00650078006500220020002F006D0069006E0069006D0069007A006500640020002F00720065006700720075006E000000
* Creates value "{871C5380-42A0-1069-A2EA-08002B30309D} {000214E6-0000-0000-C000-000000000046} 0x401=010000007C6C9C7CC0E91670A080CE01" in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached
* Creates value "{FF393560-C2A7-11CF-BFF4-444553540000} {E022B1E2-A19E-4B43-8160-7BCECACB3D6E} 0x401=0100000034003400C081DA70A080CE01" in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached
* Creates value "{FF393560-C2A7-11CF-BFF4-444553540000} {000214E6-0000-0000-C000-000000000046} 0x401=010000003400340040BBE670A080CE01" in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached
Se han cambiado múltiples claves del registro.
Aunque lo que mas me interesaba es lo que se muestra a continuación que es la parte de red, es decir, peticiones DNS, por ejemplo.
[ Network services ] * Queries DNS "serrasulshopping.com.br". * Queries DNS "ui.skype.com". * Queries DNS "www.skype.com". [ Process/window/string information ] * No changes
Aunque esta sección se trata de un análisis dinámico sin conexión a internet. He configurado con BSA, FakeNET. Este software nos ayudará en un análisis ya que si hay posibilidad de interactuar a nivel de red, FakeNET nos ayudará en eso.
En esta primera entrega hemos visto como los criminales usan sitios legítimos, como es Sourceforge para colgar archivos. En este caso han colgado una versión Fake Skype analysis, famoso programa para hacer multiconferencia, entre otras cosas.
Enlaces de interés:
[+]Pyew=> https://code.google.com/p/pyew/
[+]BSA=> http://bsa.isoftware.nl
[+]Malware analizado en Malwr=> https://malwr.com/analysis/N2E0ODA0OTYyZjcxNGQyMjkwZGU4YTgxYTQyOGY3ZWU/